EKS'pert Automation: Amazon EKS Auto Mode and Karpenter in action
Automate Your Amazon EKS Journey with Auto Mode and Karpenter in Action
Automate Your Amazon EKS Journey with Auto Mode and Karpenter in Action
Learn how Amazon EKS's new Node Health Monitoring and Auto-Repair features can help you maintain higher availability and reduce operational overhead for your Kubernetes clusters.
Discover how AWS Skill Builder can help you develop in-demand cloud skills with a variety of learning resources, including free courses, hands-on labs, and certification prep.
Explore the latest announcements from AWS re:Invent 2024, including new features for Amazon EKS and Amazon Aurora Serverless v2.
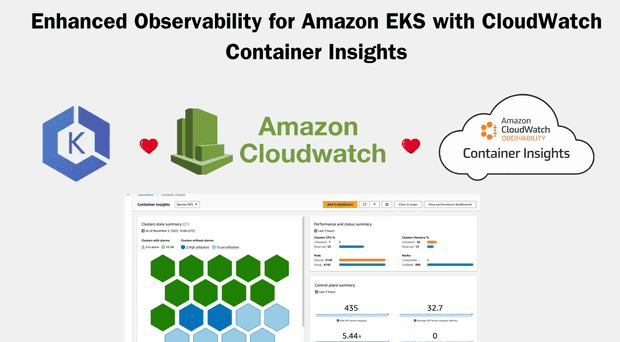
Learn how the new enhanced observability features in Amazon CloudWatch Container Insights can help you monitor and troubleshoot your Amazon EKS clusters more effectively.
Discover how Cedar by AWS can streamline the creation and management of fine-grained authorization policies, including for Kubernetes.
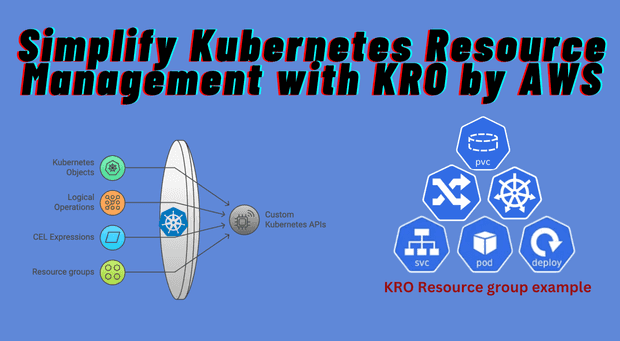
Learn how kro by AWS can simplify the creation and management of complex Kubernetes resources.
An authoritative, step-by-step guide to setting up Kubernetes 1.31 with containerd v2 runtime and Cilium for advanced networking.
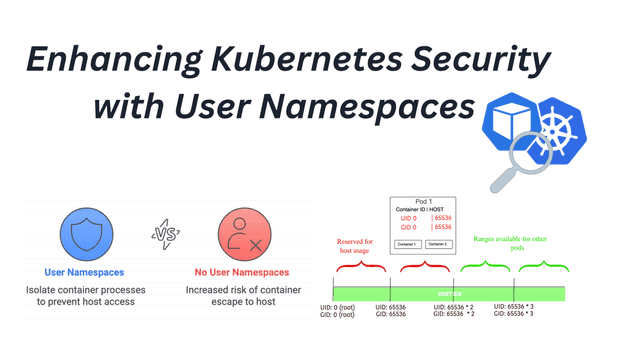
Exploring the benefits and implementation of user namespaces in Kubernetes for improved security and flexibility.
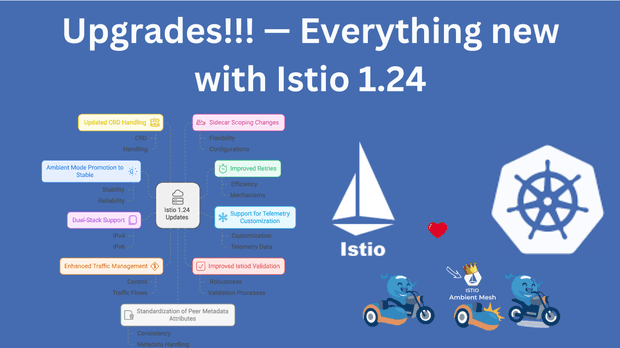
Discover the new features and enhancements in Istio 1.24, including ambient mode promotion, improved retries, and enhanced traffic management.
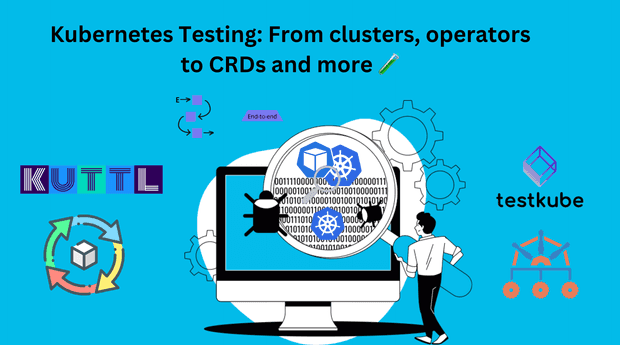
Explore the essential tools and practices for testing Kubernetes clusters and components, including application testing, cluster testing, and chaos engineering.
Learn how to accelerate your microservices development on AWS EKS using Dapr. Simplify and secure your distributed applications with ease.
An in-depth look at Dynamic Resource Allocation (DRA) in Kubernetes and its importance in modern environments
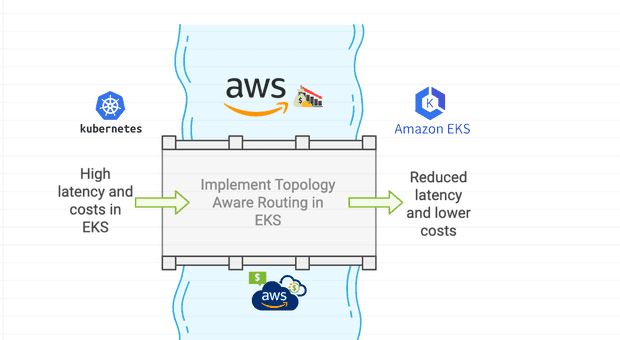
Discover how topology aware routing in Kubernetes can reduce costs and improve network performance.
Explore the real-world performance of lightning-fast in-memory databases like Redis, KeyDB, Dragonfly, and Skytable.
An epic journey from Cassandra to ScyllaDB with Rusty reinforcements, detailing how Discord scaled to handle trillions of messages.
Comprehensive step-by-step guide to securely upgrade your EKS clusters, ensuring minimal downtime and maintaining best practices throughout the process.
Building a fortress in Kubernetes: How OPA Gatekeeper and Policy-as-Code keep your cluster safe.
Simplify complex validations in Kubernetes with Common Expression Language (CEL) and Kyverno policies.
An insight into the rising star of the CNCF project, Werf, and its impact on the future of CI/CD in the DevOps landscape.
Explore the OWASP Kubernetes Top 10, a prioritized list of risks to help security practitioners, system administrators, and software developers secure their Kubernetes environments.
Master the art of multi-account, multi-region EC2 and RDS instance savings with automated management strategies, driving efficiency and cost savings.
Understand the critical role of Kubelet authorization in securing Kubernetes nodes, a must-know for Kubernetes admins.
Explore how OpenFaaS and Kubernetes are orchestrating a serverless symphony, driving innovation and efficiency in cloud-native environments.
Discover the tech-forward approach to service discovery with a deep dive into Consul on Kubernetes, exploring its role in service mesh and discovery.
Understand the risks of privilege escalation in Kubernetes RBAC and learn effective mitigation strategies to secure your cluster.
Explore the lesser-known aspects of Kubernetes, uncovering hidden features and tips that can enhance your cloud-native experience.
Explore how Cluster.dev simplifies cloud infrastructure management with declarative configurations, making it easier to manage AWS and Kubernetes environments.
Dive into the essentials of Kubernetes DNS with this guide on CoreDNS and ExternalDNS, covering the basics and advanced configuration in AWS EKS cluster.
Dive deep into the evolution of container runtimes and the Container Runtime Interface (CRI), exploring their technical intricacies and advancements.
Explore strategies to manage memory overload in Prometheus, ensuring stability and performance even when dealing with large Write-Ahead Logs (WAL).
Discover simple yet effective tricks to optimize your Docker images, reducing size and improving performance for your containerized applications.
Learn how Flagger enhances application release safety with progressive delivery, leveraging GitOps, FluxCD, and Istio for Kubernetes environments.
Discover how to effortlessly run WebAssembly workloads on Amazon EKS using SpinKube and containerd, simplifying your deployment process.
Explore the revolutionary sidecarless approach in Istio for connecting Kubernetes services, enhancing performance and simplifying networking.
Discover effective strategies and tools for optimizing costs in your Kubernetes environment, making FinOps simpler and more efficient.
Learn how to manage pod priorities and preemption in Kubernetes to ensure that your critical applications receive the resources they need, even under resource constraints.
Explore the in-place resizing feature for Kubernetes pods, allowing dynamic resource adjustments without downtime, enhancing application performance and resource management.
Discover the fundamentals of chaos engineering and how to implement chaos testing in your Kubernetes environment to enhance resilience and reliability.
Learn how to simplify the updating of ConfigMaps and Secrets in Kubernetes with Reloader, ensuring your applications always use the latest configuration.
Explore the intricacies of storage in Kubernetes, including types, configurations, and best practices for managing data in containerized environments.
How to package and deploy AWS Lambda functions as container images, enabling greater flexibility and customization beyond built-in runtimes.
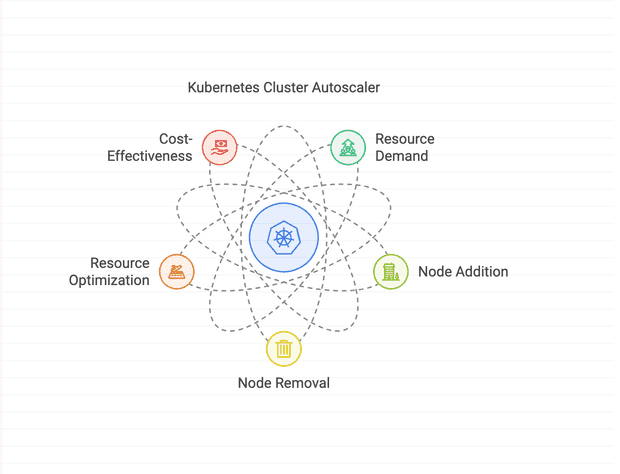
How to use the Kubernetes Cluster Autoscaler to automatically adjust your AWS EKS cluster size, optimizing both cost and performance for your applications.
Discover the importance of the CVE Vulnerability Database in DevSecOps and learn how to effectively integrate it into your security practices.
Learn how to effectively scale your Kubernetes pods both vertically and horizontally using Horizontal Pod Autoscaler (HPA) and Vertical Pod Autoscaler (VPA) for optimal resource utilization.
Pack: Dockerfile-less deployment to Kubernetes with Cloud Native Buildpacks
Explore how eks-node-viewer helps visualize dynamic node usage in EKS clusters for better optimization.
Explore the capabilities of VictoriaMetrics as a powerful time-series database, its comparison with Prometheus, and how to effectively implement monitoring in Kubernetes.
How to enhance the security of your monitoring stack using a dead man switch, ensuring that your systems are always under watchful eyes.
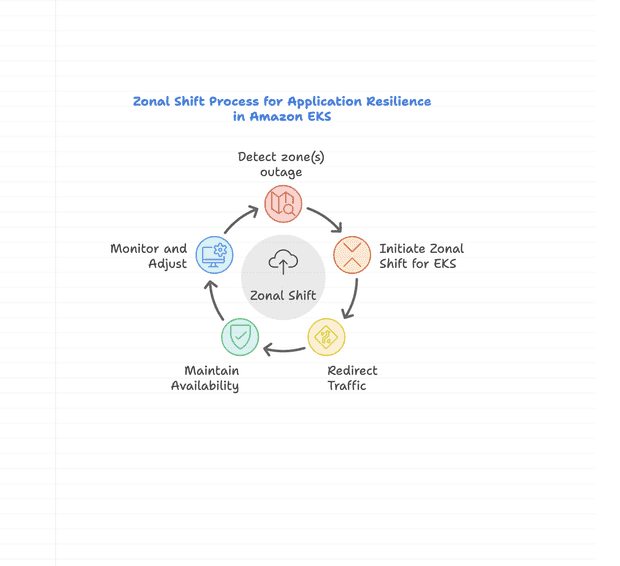
Learn how ARC Zonal Shift improves application availability in Amazon EKS during outages.
Explore how to implement OIDC authentication with Okta in Vault to enhance security and streamline access control for your applications.
How to protect your Docker applications with secure base images, ensuring consistency and reliability in your cloud environment.
Turning Kubernetes into a Developer-Friendly Platform with Cyclops.
Discover how Skaffold streamlines Kubernetes deployments, automating container image updates and saving valuable time.
Explore how Submariner enables seamless connectivity between Kubernetes clusters.
Learn how to secure your CI/CD pipelines by signing and verifying container images using Docker, Cosign, and Kyverno.
Explore how to audit Tetragon logs for enhanced eBPF log analytics in Kubernetes.
Discover Netflix's innovative approach to empowering developers through the concept of paved roads, fostering both freedom and responsibility.
Learn how to leverage Amazon EKS, KEDA, and Karpenter for scalable and cost-effective event-driven workloads.
Explore effective strategies for pod scheduling in Kubernetes to optimize resource utilization.
Discover how ephemeral environments can enhance your CI/CD pipelines using Kubernetes.
Discover how K8ssandra simplifies the management of Apache Cassandra on Kubernetes for seamless data handling.
Learn how to use Strimzi to run Apache Kafka on Kubernetes for efficient data streaming.
Explore KubeArmor, a great runtime security enforcement system designed to protect cloud-native applications in Kubernetes environments.
Learn best practices and tools for managing deprecated Kubernetes APIs effectively.
Discover effective tools and strategies to enhance container image availability and speed through caching in Kubernetes.
Learn how to effectively scale Kubernetes workloads using Istio metrics and the Horizontal Pod Autoscaler for optimal performance.
Discover how Carvel kapp simplifies Kubernetes application management, giving you control over your Kubernetes resources.
Discover how Argo Workflows can simplify the management of parallel jobs in Kubernetes, enhancing efficiency and scalability.
Learn how to optimize resource spend with the Mayfly Kubernetes Operator, implementing FinOps best practices for ephemeral resources.
Learn how to optimize Kubernetes resource allocation with Goldilocks, ensuring your resource requests and limits are set just right.
Explore how to automate and orchestrate data workflows in Kubernetes using Amazon managed Apache Airflow MWAA.
Explore how Kubernetes simplifies the deployment and scaling of AI/ML models on EKS.
EKS, Databases, Cloud Native DB, CloudNative-PG, PostgreSQL, Ceph Rook
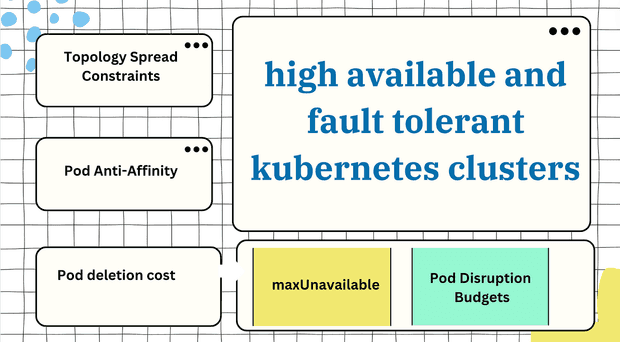
Discover the hidden gems within Kubernetes that ensure your clusters remain highly available and resilient.
Learn how Sysdig and Docker's new alliance, featuring Docker Scout, aims to enhance cloud-native security with prioritized risk management and improved security posture.
Learn how to automate Terraform code checks and enforce security standards using pre-commit hooks, saving time and improving code quality.
How to secure your Kubernetes applications using Okta for OIDC, Istio for service mesh, and OAuth2-Proxy for authentication.
Explore how Kubernetes Admission Controllers enhance security and control within your clusters, providing a comprehensive guide to their implementation and benefits.
Explore how Kubernetes Admission Controllers enhance security and control within your clusters, providing a comprehensive guide to their implementation and benefits.
Learn how Kubefirst simplifies the deployment of production-ready Kubernetes platforms with a GitOps-driven approach.
Explore the transition from Ingress to Gateway API and Cilium for modern Kubernetes traffic management.
Discover how Kubewatch enhances Kubernetes observability and monitoring with real-time insights and alerts.
Unlock the secrets to managing Docker images efficiently by understanding and utilizing Docker layers.
Discover how the Vault Agent Injector can securely inject secrets into your Kubernetes pods, enhancing the security of your Kubernetes secrets management.
Gain a comprehensive understanding of Kubernetes API groups and versions, and learn how they help manage and extend Kubernetes functionality.
Learn how to reverse-engineer Docker images back into Dockerfiles, providing insights into the process and tools needed for effective backtracking.
Enhance your EKS cluster by integrating Istio and Cilium for improved networking and security. Learn how these tools can optimize your Kubernetes environment.
Discover how Terragrunt can revolutionize your Terraform workflow by keeping your code DRY and maintainable. Learn best practices and tips for efficient infrastructure as code (IaC) management.
Learn Kubernetes open standards and understand the key components like OCI, CRI, CNI, CSI, SMI, CPI, KSD, and CIL that are shaping the future of container orchestration.
Learn how Helmfile provides a declarative approach to managing and deploying Helm charts, making your Kubernetes application management more efficient and maintainable.
How to securely manage Kubernetes passwords using Sealed Secrets. This guide covers one-way encryption techniques to protect your sensitive data.
Explore how to achieve GDPR and ISO 27001 compliance in Kubernetes. Get essential tips for enhancing security and observability in your production workloads.
Discover the benefits of contributing to open source projects and learn how to get started. Make a positive impact in the open source community with these practical tips.
Learn how to effectively monitor your Kubernetes clusters using kube-state-metrics. This comprehensive guide covers the setup, usage, and benefits of KSM for cluster observability.
Discover essential tricks and tools to solve all your Kubernetes debugging needs like a pro. Reduce friction and frustration with these expert tips.
Discover Arkade, the open-source marketplace for developer tools. Learn how this one-stop-shop for CLI tools can enhance your Kubernetes development experience.
Learn how the Cluster Proportional Autoscaler (CPA) can help you scale your Kubernetes cluster efficiently. This guide covers the benefits and implementation of CPA to match your growing infrastructure needs.
Discover user-friendly desktop Kubernetes open-source development environments. Learn how these tools make Kubernetes cluster management accessible and simple for everyone.
Discover how Cloud Native Operational Excellence (CNOE) can simplify platform engineering. Learn to build better software tools with cloud-native technologies and community-driven best practices.
Explore the forensic capabilities of container checkpointing with CRIU in Kubernetes. Learn how to use the Kubelet checkpoint API for stateful container copies and enhance your security posture.
Explore whether learning Kubernetes is the right choice for you. Understand its importance, benefits, and how much you need to know to get started.
Discover the best tools and solutions for local Kubernetes development. Enhance your k8s development experience with these practical tips and tools.
Ensure reliable DNS resolution in Amazon Kubernetes clusters by monitoring CoreDNS performance. This guide covers essential metrics and best practices for effective DNS monitoring.
Build container images directly within your Kubernetes cluster using Kaniko. This guide covers the benefits of daemonless Docker image building in Kubernetes.
Learn how to use Kubernetes probes to improve the health checks of your applications. This guide covers liveness, readiness, and startup probes to ensure your apps run smoothly.
Discover MKAT, the Managed Kubernetes Auditing Toolkit from DataDog. Learn how this powerful tool enhances security and compliance in your Kubernetes environments.
Get started with Backstage, the open-source platform for building developer portals. This guide introduces Backstage and its key features, helping you streamline your development workflows.
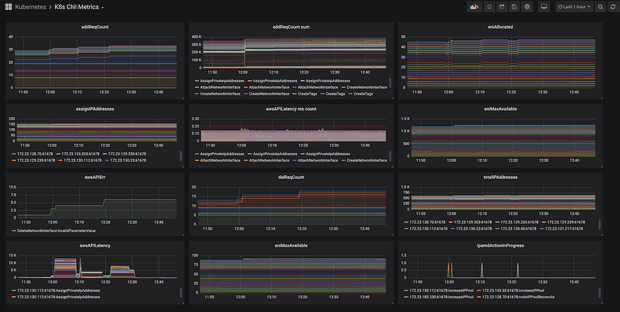
Explore the CNI Metrics Helper for the Amazon VPC CNI Plugin and how it enhances network monitoring in Kubernetes. This guide covers its features and benefits for efficient network management.
Explore the fundamentals of platform engineering and how it simplifies software development. This introduction will guide you through the key concepts and benefits.
Learn about the common exit codes and error messages you might encounter in containers and Kubernetes. This guide will help you troubleshoot and resolve issues effectively.
Discover the power of Helm Chart Hooks and how they can automate and streamline your Kubernetes deployments. Learn about the different types of hooks and their practical applications.
Dive into the diverse world of cloud-native technologies, exploring Kubernetes and beyond. Understand the dynamic landscape and how these tools can revolutionize your DevOps practices.
Learn how to secure end-to-end traffic on Amazon EKS using Istio, ALB, and ACM with TLS certificates. This guide covers the essential steps and best practices for implementing robust security measures.
Explore how to programmatically configure and deploy Kubernetes clusters using Cluster API (CAPI).
Discover how Botkube simplifies Kubernetes management and automation. Learn about its features, benefits, and how it can streamline cluster operations for everyone.
Explore how Dapr provides a portable, event-driven runtime for building distributed applications on Kubernetes. Learn about its features, benefits, and best practices for leveraging Dapr in your cloud-native projects.
Discover effective practices to avoid IPv4 address exhaustion in Amazon EKS clusters.
Explore the integration of WebAssembly (Wasm) with Kubernetes for cloud-native application deployment. This first part of the series covers the basics and benefits of using Wasm on K8s.
Learn how to enhance security and compliance in EKS by detecting manual actions using Terraform and SNS.
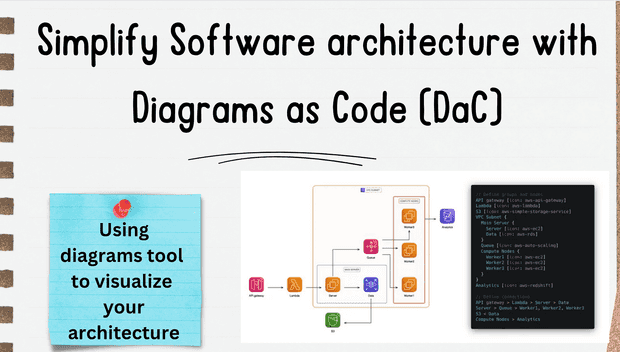
Simplify your software architecture with Diagrams as Code (DaC) using Python. This guide covers tools and techniques to visualize your architecture effectively.
Discover how Velero simplifies EKS backups, ensuring data protection and recovery.
Discover how Amazon GuardDuty enhances the security of your Amazon EKS environment. Learn about its features, benefits, and best practices for maintaining a secure Kubernetes cluster.
Learn how to uncover hidden AWS costs and spot idle resources with unusd.cloud to save money and reduce risk.
Explore how Semantic Release and SemVer can automate version management and streamline release strategies. Learn best practices for maintaining consistency and reliability in your software projects.
Ensure the quality and resilience of your AWS Lambda functions with Python and Moto for effective unit testing.
Dive into Amazon EKS with hands-on labs designed to give you a practical introduction to this powerful service.
Automate Kubernetes monitoring using Terraform and Datadog for better observability and infrastructure management.
How AWS Controllers for Kubernetes (ACK) enables seamless management of AWS services directly from your Kubernetes cluster.
Detect threats in AWS EKS audit logs with Falco
Explore how AWS EKS Security Groups Per Pod can enhance the security of your Kubernetes clusters by providing fine-grained network policies.
Explore how Cloud Custodian enables compliance as code and auto-remediation to enhance your cloud security posture.
Discover how k8s-pvc-tagger can streamline your AWS EBS tagging process and enhance your cost management strategies. This tool acts as a versatile solution for efficient resource management in Kubernetes.
Securing Kubernetes involves robust runtime security and system hardening. Learn how tools like Strace, Falco, AppArmor, and Seccomp can protect your clusters.
Dive deeper into Kubernetes networking with the Gateway API and learn how to optimize AWS EKS networking through VPC Lattice integration. This second part of the series continues to explore advanced concepts and practical implementations.
How to use SOPS to securely manage your secrets in Git. This guide provides a foolproof method to ensure your sensitive information remains protected.
Explore how the Gateway API redefines Kubernetes networking, enhancing connectivity and security in k8s clusters. This first part of the series dives into the fundamentals and benefits.
Secure your software supply chain by using AWS Signer to sign and validate OCI artifacts and ensure the integrity and authenticity of your containerized applications and metadata.
Build a monitoring solution for AWS EKS using open source tools like Grafana, Prometheus, AlertManager, Promtail, and Loki.
Get to know the secrets of Kubeconfig and EKS authentication with AWS
Explore how AWS CloudWatch Container Insights can help you monitor EKS cluster metrics and logs, providing proactive insights for better cluster management.
Explore the differences between AWS Instance Metadata Service v1 and v2, and understand their impact on Kubernetes Pods and Docker Containers. Enhance your AWS environment security with this comprehensive analysis.
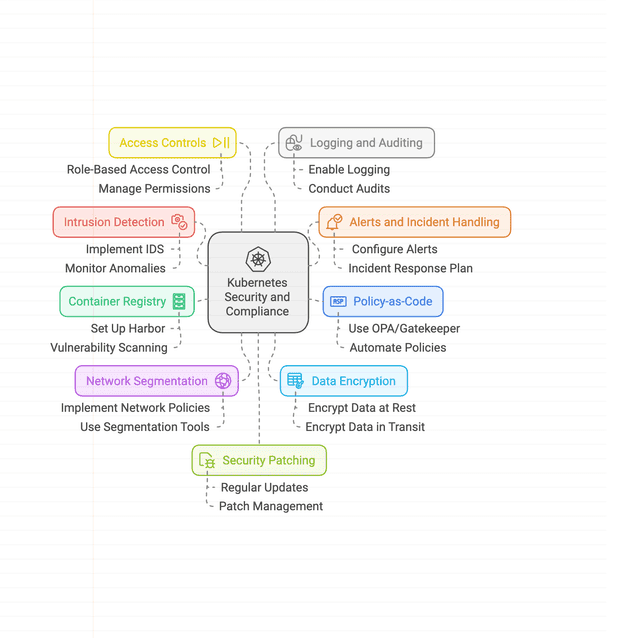
Learn about essential security assessment guidelines and checklists for Kubernetes, ensuring your clusters are secure and compliant with best practices.
Discover essential tips for managing Amazon EKS, focusing on cost-saving strategies and performance enhancement to optimize your Kubernetes clusters.
Gain real-time insights into AWS cost monitoring and FinOps using Cost Explorer and Slack ChatOps, making your financial operations easier and enhancing cost efficiency.
Master the art of troubleshooting in AWS by building effective strategies, utilizing logs, and leveraging monitoring tools to identify and resolve issues efficiently.
Learn the best practices for monitoring your AWS environment using CloudWatch, ensuring you stay ahead of potential issues and maintain optimal performance.
Learn how to build a resilient AWS architecture with a focus on performance and reliability optimization, ensuring your cloud infrastructure is robust and efficient.
Explore a curated set of Amazon EKS add-ons designed to enhance the management and functionality of your Kubernetes clusters, integrating seamlessly with tools like Terraform and CDK.
How to accelerate your Kubernetes cluster deployment using EKS Blueprints, providing a streamlined and efficient setup process for AWS EKS.
How to proactively manage AWS service limits using AwsLimitChecker, ensuring your applications stay within bounds and avoid disruptions.
How to use EKS control plane logs and AWS CloudTrail logs to gain visibility into your cluster’s activities, detect potential security threats, and investigate incidents.
Various open-source tools designed to detect and manage drift in Terraform-managed infrastructure, ensuring consistency and reliability in your cloud environment.
How to automate compliance with best practices for Amazon EKS, ensuring your clusters remain secure and compliant with industry standards.
Learn how to simplify AWS permissions for your EKS workloads using EKS Pod Identity, providing an easy and secure way to grant AWS access.
Simplify Kubernetes management using Infrastructure as Code (IaC) tools, focusing on automation, security, and scalability for your Kubernetes infrastructure.
Learn how to enable distributed tracing for containerized applications using AWS X-Ray, providing end-to-end performance visibility and insights into your workloads on AWS.
Explore the capabilities of generative AI on AWS, focusing on tools like SageMaker and Bedrock to enhance your AI development and deployment processes.
A comprehensive walkthrough on building Helm charts from scratch, covering essential concepts and best practices for effective network management in Kubernetes.
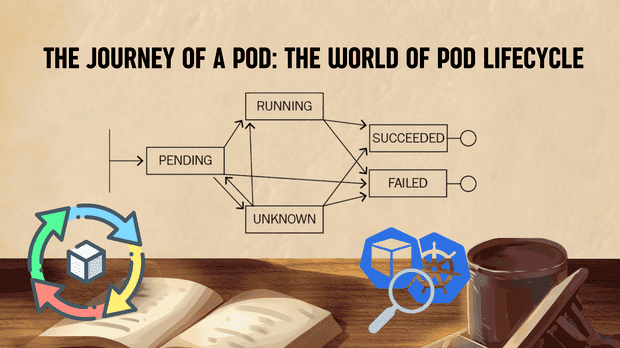
The journey of a pod through its lifecycle involves several key states, each critical to its functionality and performance.
Explore the essential yet often overlooked components of Kubernetes networking. This guide sheds light on Kube-Proxy and Container Network Interface CNI
Discover Kubernetes networking and how DNS plays a major role in enabling communication between pods, mechanisms behind service discovery and the architecture that supports pod interactions within a Kubernetes cluster.
Modular Docker builds, Devcontainer Integration,Nix Package Manager, Home-Manager, Dotfiles
replicable Setups, Devcontainer,Nix Package Manager, Home-Manager, Minimize local machine dependencies
Discover 11 cool kubectl plugins that can enhance your Kubernetes management experience, offering additional functionality and efficiency.
AWS, consistent tagging of resources, best practices, cost tracking, lifecycle management
EKS, AWS, Secrets Manager, Kubernetes, Security
kubernetes cluster, Operating system, Talos OS, RancherOS, AWS Bottlerocket
EKS Access Entries, Terraform, OpenTofu, Kubernetes, Authentication
AWS SDK for Python, Boto3, Pod identity agent, EKS
AI, Kubernetes, Open Source Tools, AI/OpenAI for Kubernetes
Kubernetes, Anti-Patterns, Cloud Native, Best practices
EKS, Databases, Cloud Native DB
Logs, metrics, traces collection in OTel SDK
Discover the key improvements in Kubernetes 1.30, including security enhancements, resource management, and more.
Explore the new features in Kubernetes 1.28, including built-in support for sidecar containers, job optimizations, and better proxies.